Cyber Essentials Plus is the highest level of certification available under the UK’s National Cyber Security Centre (NCSC) backed Cyber Essentials Scheme. The scheme helps organisations ensure they have effectively implemented the essential security controls to protect against common cyber threats.
Building upon the baseline Cyber Essentials certification, where organisations self-assess their security controls using a questionnaire, the Cyber Essentials Plus certification involves a hands-on evaluation by a skilled technical security consultant. This process offers organisations a cost-effective way to identify flaws in their security controls. For more information on the pricing of Cyber Essentials and Cyber Essentials Plus, please click here.
The latest change to the Cyber Essentials scheme ‘Montpellier’ went live on 24th April 2023. There have since been no substantial changes to the scheme requirements and IASME who manage the scheme have not announced any upcoming changes for 2024. In this guide we’ll explore the requirements to achieve certification, how much certification costs and what preparations can be made to pass the assessment first time.
Cyber Essentials Plus Scoping Guidelines for 2024
The Cyber Essentials Plus scope is based upon the information provided in the baseline Cyber Essentials questionnaire. It is recommended that the scope include the whole organisation where possible, but it can be refined to a single network or to exclude certain networks (a subset of the organisation) where required.
All devices and software within the scope that meet any of the following criteria will need to adhere to the scheme requirements:
- can accept incoming network connections from untrusted internet-connected hosts
- can establish user-initiated outbound connections to devices via the internet
- control the flow of data between any of the above devices and the internet
All cloud services that host organisation data or services will also fall into scope (including SaaS, PaaS and IaaS services).
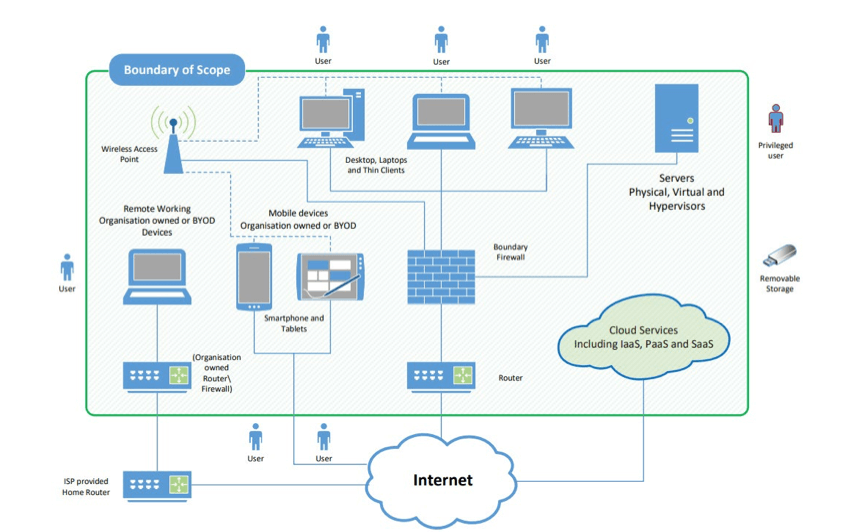
There are some additional circumstances where BYOD devices/devices owned by a third party will fall out of scope for the assessment. Please see the scoping table below:
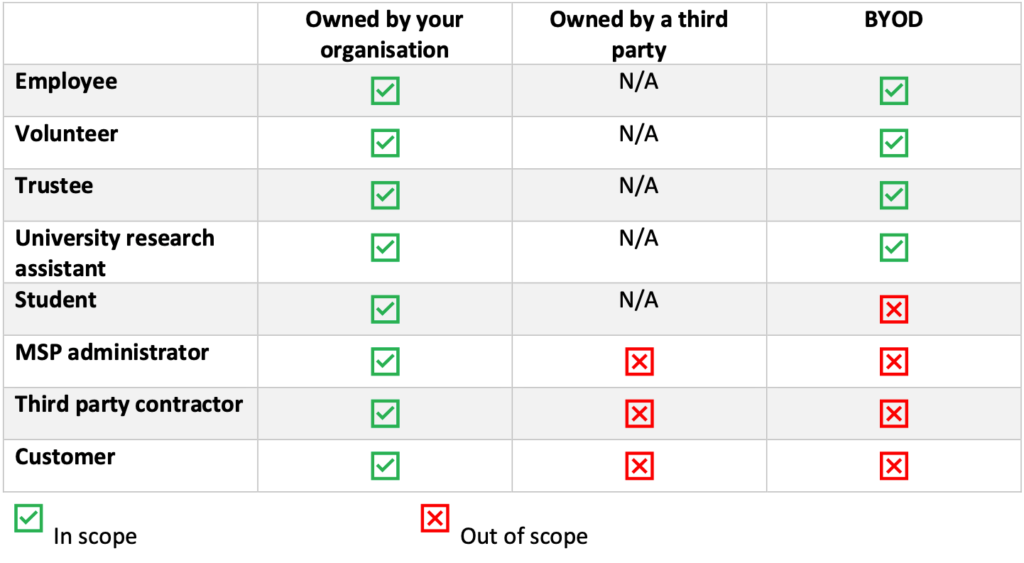
For expert advice on how to scope your Cyber Essentials/Cyber Essentials Plus assessment, please contact us for a free consultation. More information can also be found here: Cyber Essentials: Requirements for IT Infrastructure v3.1.
What’s Involved in Cyber Essentials Plus Certification?
To obtain Cyber Essentials Plus certification, your organisation must undergo a hands-on technical assessment, which must be completed within three months of passing the baseline Cyber Essentials certification. This assessment involves a range of checks, all of which must meet compliance standards for the certificate to be granted. The process for achieving Cyber Essentials Plus is outlined as follows:
- The applicant organisation completes the Cyber Essentials questionnaire and obtains the basic certification.
- The questionnaire determines the number of devices and servers to be sampled for the Cyber Essentials Plus assessment (servers only require a vulnerability scan, not full checks).
- Your assessor will provide the necessary preparations for the assessment, including obtaining your internet-facing IP addresses and offering installation guides for software required on sampled machines.
- The assessment is conducted by your assessor (the checks are outlined in the following sections). Your organisation will either pass the assessment or receive feedback on areas requiring remediation to achieve scheme compliance.
- The applicant organisation addresses the feedback and proceeds to repeat step 4.
External Network Vulnerability Scan
An external network vulnerability scan is conducted against all public-facing IP addresses to identify security issues on your external network perimeter. The scan will identify issues such as misconfigurations, unpatched/end-of-life software and authentication mechanism weaknesses.
Any vulnerabilities found which are high/critical risk (base CVSSv3 score of 7.0 of above) will need to be remediated to achieve certification.
The internet-facing services will also be evaluated to check that basic security controls have been implemented.
Credentialed Patch Scan on Devices/Servers
A credentialed patch audit will need to be run against a sample of devices and servers (where a desktop GUI exists) to identify unpatched or end-of-life software on the machines that could be exploited by an attacker.
Any patch-related vulnerability identified which is high/critical risk (base CVSSv3 score of 7.0 of above) and where a patch has been released over 14 days ago will need to be remediated to pass the check. Any identified software that is end-of-life will also need to be remediated.
Where a patch has not been released or was released within 14 days of the scan being conducted will be compliant under the scheme.
Testing Malware Protections
For workstations, the anti-virus software engine will be checked to ensure that it’s been updated within the last 30 days and that the signatures have been updated within the last 24 hours.
For mobile devices, the assessor will run through several checks to ensure that the device has been effectively configured to prevent malware from being downloaded and installed on the device (including checks against device certificates and Android special installation permissions).
Testing Email Client Protections Against Executables/Malware
Each workstation’s email client will undergo evaluation to verify that effective protections are in place against malicious executables and malware. Various files, including test malware (EICAR) and executable attachments such as .exe, .bat, .msi, .py, and .sh files, will be sent to the user’s mailbox.
Malware files must be filtered before reaching the user’s mailbox, while additional executables should require a prompt or an opportunity for the user to assess the action before execution via the email client.
Testing Web Browser Protections Against Executables/Malware
The installed web browsers on each workstation will also be evaluated to ensure their protections against malicious executables/malware.
The assessor will attempt to download and execute various test malware files for each web browser. Ideally, these files should be blocked upon download. However, if they are downloaded but blocked on execution, this will also be compliant. The assessor will also attempt to download and execute various file types, similar to the email client checks. The goal is to observe a prompt displayed, enabling the user to assess their action before execution occurs.
Testing for Multi-Factor Authentication Enforcement in Cloud Services
The assessor will assess the cloud services accessible by each device owner (such as Google Workspace or MS Office 365) to identify whether multi-factor authentication is enforced. This check often includes asking the user to log into the cloud services to show that an MFA prompt is displayed.
MFA must be enforced for all organisation users across all cloud services where an MFA option exists to pass this check.
Testing for Account Separation
The assessor will ensure that the regular user accounts on sampled workstations do not possess administrator privileges, as such elevated access should only be employed when essential. Additionally, device owners with administrator privileges must maintain a separate standard user account for routine activities such as accessing emails and browsing the internet.
Why Become Cyber Essentials Plus Certified?
Stakeholder Requirements:The demand for Cyber Essential Plus is growing within the supply chains of both public and private sector organisations. Obtaining this certification shows your commitment to strong cyber security practices.
Cost Effective: Cyber Essentials Plus can be a cost-effective next step following basic Cyber Essentials certification and verifies that you have the fundamental controls in place to protect your organisation against a range of common cyber threats.
Clear Security Recommendations: You will receive feedback on how your organisation can further improve its overall security posture.
Certificate and Logo: Achieving Cyber Essentials Plus certification permits your organisation to display the Cyber Essentials Plus logo which can be placed on your website and social media to demonstrate that you take security seriously.
Preparing Your Organisation to Pass Cyber Essentials Plus
Cyber Essentials Plus is designed to be accessible by all organisation regardless of size and industry. With some initial preparation, you’ll be ready to get the most out of the assessment and pass first time. Below are some key actions that can be taken in preparation for your Cyber Essentials Plus assessment:
Update Your Devices/Servers and Their Software
Ensure that all software on your devices and servers has been patched to the latest version and that any end-of-life software has been removed or upgraded. A few days before the assessment, take some time to check that your organisation’s software is up to date and that no unsupported software exists. It’s important to apply high and critical-risk security patches within 14 days of release. This will reduce the risk of unpatched software being detected during the vulnerability scanning.
Check Your Anti-Virus Software Configuration
Ensure that the anti-virus software on your devices and servers is up to date and that the signatures are being updated within a 24-hour window. All automatic updates should be enabled where the option is provided. You should also verify that your antivirus software is scanning files on access (and ideally on download).
Check Your Internet-Facing Services
Ensure that any services that are internet facing have been disabled where no longer required. Where any internet-facing services require authentication to access organisation/user data, make sure that the default password has been changed and the service mitigations in place against brute-force attacks. This includes an account lockout policy and/or enforcing multi-factor authentication. Where an account lockout mechanism or a form of throttling has been applied, ensure that a user is restricted to making no more than 10 attempts within a 5-minute period.
Ensure Multi-Factor Authentication is Enforced for All Cloud Service Users
Ensure that multi-factor authentication has been enforced for all users across all cloud services that hold organisation data (where an MFA option exists). MFA is exclusively offered through a premium subscription or requires integration with another authentication service like MS Azure, its implementation will be necessary to ensure compliance.
Ensure Account Separation is Enforced for User Accounts
Ensure that workstation owners who have access to administrative user account also have a standard user account which is used for day-to-day work. Workstation owners must only use the administrative account where conducting necessary privileged tasks such as installing software. Please ensure that accounts are not being shared between users.
How Much Will Cyber Essentials Plus Cost?
The cost of Cyber Essentials Plus will be dependent on the Certification Body.
Predatech offers Cyber Essentials Plus assessment and certification from £1,100+VAT (dependent on organisation size). This includes any support required as well as any re-testing (if applicable).
Please note, Cyber Essentials Plus does require a valid Cyber Essentials certificate (issued in the last three months), and pricing for this can be found here.
Predatech is a CREST-accredited organisation and a certification body for Cyber Essentials & Cyber Essentials Plus. If you are interesting in achieving or renewing your Cyber Essentials Plus certification, click here to find out more about our approach or contact us today for a free consultation.



