The words ‘cyber’ and ‘attack’ often bring fear into the hearts of business owners and IT managers alike. For most businesses, especially smaller ones, knowing what to do and where to look when it comes to cyber security can be a real challenge.
Penetration testing is a valuable tool in your cyber security arsenal because of its in-depth nature. It can help you to improve your security posture and identify the hidden weaknesses that attackers may use to exploit your IT systems, networks, and applications.
What is a Penetration Test?
A penetration test (commonly abbreviated to ‘pentest’) is an authorised and in-depth manual assessment of a business’s IT systems, simulating the same actions and techniques that might be employed by an attacker. This can help a business better understand where their vulnerabilities are and how to successfully remediate them so they can’t be exploited by attackers in the future.
Why is Penetration Testing important?
A 2019 report found that security breaches had increased by 67% since 2014, and the number of breaches is forecast to continue increasing over the coming years as data becomes even more valuable and technology becomes even more integral to peoples’ lives.
Penetration testing provides the most in-depth form of security testing and it can therefore help a business remediate their weaknesses so they are more resilient to an attack. This will also make a business a less attractive target to attackers looking for an easy win.
What Penetration Testing approaches are there?
Penetration testing is often categorised into three different approaches:
- Black Box Testing: With this approach, the penetration tester conducts the engagement with no knowledge of how systems, networks, and applications work internally. This is often the most realistic approach, however black box testing can result in fewer vulnerabilities being discovered as most penetration tests will have time/cost constraints.
- White Box Testing: With this approach, the client will provide the tester with all the information they need to ensure they understand how systems, networks, and applications work internally, and this may include providing credentials. This is a very unrealistic approach to testing but is often the fastest method and can therefore be the cheapest.
- Grey Box Testing: Although black and white box testing approaches are regularly discussed in a binary way, realistically the pentesting approach will sit somewhere in between. Grey box testing is commonly referred to as the middle ground between black and white and is typically the most effective where a company wants to identify and address practical vulnerabilities that could potentially be used by attackers, using realistic scenarios. Most of Predatech’s testing will fit into this category.
What methodology does Penetration Testing follow?
Testers often structure a testing engagement built upon methodologies such as the Open Source Security Testing Methodology Manual (OSSTMM), the Penetration Testing Execution Standard (PTES), and NIST SP 800-115, supplemented by domain-specific methodologies such as the Open Web Application Security Project (OWASP) Top 10 and the OWASP Web Standard Testing Guide.
The penetration testing formula will change depending on the testing domain and the company conducting the pentest, however, most testing will align with these 6 stages:
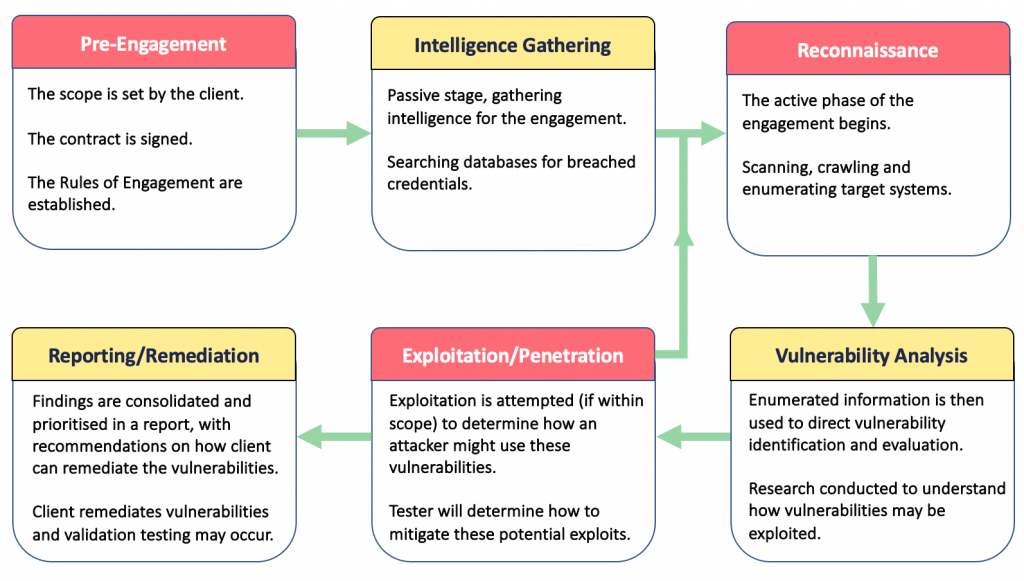
What else do you need to know?
Penetration testing is just a snapshot in time of your business’s security posture and so penetration testing should ideally be done on a regular basis (or when there has been a major change to your systems, application, or network) supplemented by recurring vulnerability assessments between tests.
Does my business need Penetration Testing?
Some businesses are a more attractive target to attackers, for example, those holding sensitive data like credit/debit card information or those that have a high profile online. However, any business can become a target regardless of its size, and it’s therefore important to harden your IT systems in case the worst were to occur. Some businesses may decide to meet halfway and commission an automated vulnerability assessment, which may make sense for businesses where they perceive their risk to be low. This is a completely valid option.
When in doubt, contact a penetration testing provider where an expert can discuss your business profile and recommend the most beneficial solution for your business.
If you’re interested in a free consultation, get in touch with us at [email protected], we’d love to hear from you.




