*We’ve written a new guide to Cyber Essentials Plus certification which reflects the up-to-date requirements*.
Cyber Essentials Plus is the highest level of certification that can be achieved under the UK’s National Cyber Security Centre (NCSC) backed Cyber Essentials Scheme. The scheme helps organisations ensure they have effectively implemented the fundamental security controls to protect them against common cyber attacks.
While the baseline Cyber Essentials certification involves an organisation self assessing their security controls using a questionnaire, the Cyber Essentials Plus certification requires a hands-on evaluation by a skilled technical security professional. This provides organisations with a cost-effective way to identify flaws in their basic security controls. To find out more about the cost of Cyber Essentials & Cyber Essentials Plus, please click here.
On the 24th April 2023, the newest update to the Cyber Essentials scheme, ‘Montpellier’ goes live, introducing new requirements that will affect both the Cyber Essentials and Cyber Essentials Plus assessments. In this guide, we’ll take a look at the key changes affecting Cyber Essentials Plus this year and how much certification costs.
Key Cyber Essentials Plus Changes for 2023
MFA Requirements for Cloud Services: One of the most significant changes to the scheme is that multi-factor authentication (MFA) is now required for all users across all cloud services. Whereas previously only admin users were mandated to have MFA enforced, this has now been extended to standard users. This may increase the number of MFA checks required during a Cyber Essentials Plus assessment.
Changes to Malware Protection Checks: Previously the Cyber Essentials Plus assessment focussed on assessing signature-based anti-malware protections, which meant that if an antivirus software was non-heuristic (detected malware based on methods not using malware signatures), the organisation would fail the check. However, the new scheme introduces accepted methods of assessing malware protection software that is not signature based.
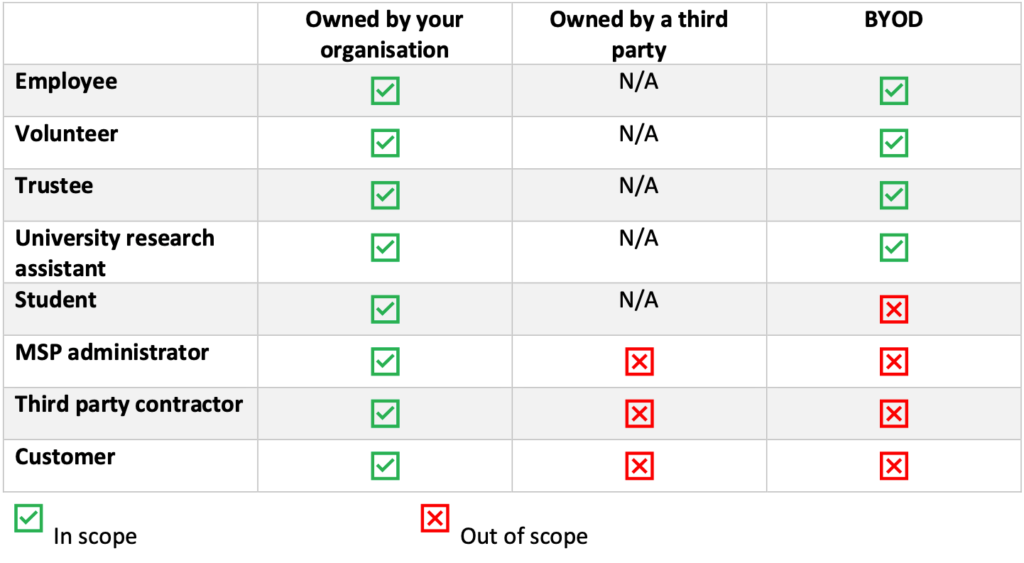
Changes to Scoping Guidelines: The new scheme provides clearer guidance around the devices that fall out of scope for the assessment. This makes it simpler to identify which devices will need to be listed on your Cyber Essentials questionnaire and sampled during your Cyber Essentials Plus assessment. Please see the scoping table below to see whether particular devices will fall into scope:
What does Cyber Essentials Plus Certification involve?
In order to achieve Cyber Essentials Plus certification, you must undertake and pass a hands-on technical assessment (and this must be completed within three months of passing your Cyber Essentials certification). The Cyber Essentials Plus assessment includes a number of checks, all of which must be compliant in order for the certificate to be awarded. The typical process for achieving Cyber Essentials Plus is as follows:
- The applicant organisation completes the Cyber Essentials questionnaire and achieves the basic certification.
- The questionnaire is then used to calculate the number of devices and servers that will need to be sampled for the Cyber Essentials Plus assessment (servers only require a vulnerability scan not the full checks).
- Your assessor will send over the necessary preparations to facilitate the assessment including obtaining your internet-facing IP addresses and providing installation guides for software that needs to be installed on sampled machines.
- The assessment is undertaken by your assessor (the checks are detailed in the sections below) and your organisation will either pass the assessment or the assessor will provide feedback on what needs to be remediated in order to achieve compliance with the scheme.
- The applicant organisation addresses the feedback and then step 4 restarts.
External Network Vulnerability Scan
The assessor will conduct an external network vulnerability scan on your organisation’s public IP addresses to identify vulnerabilities in your internet-facing services. In order to be compliant with the scheme, all high or critical-risk vulnerabilities (those with a CVSSv3 score of 7.0 or higher) will need to be remediated. An evaluation will also be conducted on the internet-facing services identified to check that basic security controls have been implemented.
Device/Server Vulnerability Scans
The assessor will scan all sampled workstations and servers that have a desktop GUI (i.e. those that are not purely command line based) to identify patch related vulnerabilities that could be exploited by attackers. Any high or critical-risk vulnerabilities that relate to unpatched software (where the patch was released over 14 days ago) will need to be remediated in order for the organisation to pass this check.
Testing General Malware Protections
The assessor will check the antivirus software installed on in-scope workstations to ensure it’s up to date and the signatures are up to date (where signature-based). The antivirus engine is expected to have been updated in the last 30 days and the signatures should have been updated in the last 24 hours.
For mobile devices, the assessor will run through a number of checks to ensure that the device has been effectively configured to prevent malware from being downloaded and installed on the device (including checks against device certificates and Android special installation permissions).
Testing Email Client Protections against Executables/Malware
For each workstation, the assessor will send a number of emails, each containing an attached file to the user’s email address. These files include test malware files as well as a range of executable attachments (such as .exe, .bat, .sh, .py and .jar files). The malware files should be filtered before they reach the user’s mailbox and the additional executables should not be able to execute from the email client without first displaying a prompt or presenting an opportunity for the user to evaluate the action being taken.
Testing Web Browser Protections against Executables/Malware
For each web browser installed on the sampled workstations, the assessor will firstly attempt to download and execute a range of test malware files. Ideally, these should be blocked on download, however, if they do download but are blocked on execution this is also compliant. Secondly the assessor will attempt to download and execute a range of different file types (similar to the email client checks) and will be looking to see a prompt displayed allowing the user to evaluate their action before execution can take place.
Testing for Multi-Factor Authentication
The assessor will assess the cloud services accessible by each device owner (such as Google Workspace or MS Office 365) to identify whether multi-factor authentication is enforced. This check often includes asking the user to log into the cloud services to show that an MFA prompt is displayed.
Testing for Account Separation
The assessor will verify that the day-to-day user account for each sampled device does not have administrator privileges, since administrator accounts should only be used when necessary. Device owners who have access to an administrator account must also have a standard user account which they use for day-to-day activities such as accessing emails and browsing the web.
Why Become Cyber Essentials Plus Certified?
Customer Requirements: Cyber Essential Plus is becoming more commonly mandated in the supply chains of both public and private sector organisations and it demonstrates your commitment to good cyber security practices.
Cost Effective: Cyber Essentials Plus can be a cost-effective next step after achieving your basic Cyber Essentials certification and can verify you have the fundamental controls in place to protect your organisation against a range of common threats.
Clear Security Recommendations: You will receive recommendations and areas for improvement to help your organisation improve its overall security posture.
Certificate and Logo: Passing your Cyber Essentials Plus certification means that you will also earn the right to use the Cyber Essentials Plus logo which can be displayed on your website and social media to demonstrate that you take security seriously.
Preparing your Organisation to Pass Cyber Essentials Plus
Cyber Essentials Plus is designed to be accessible to organisation of all sizes and across all industries, and with a little preparation, you can be ready to get the most out of the certification and pass first time. Here are some of the key actions you can take to prepare for your Cyber Essentials Plus assessment:
Update your Device/Servers and their Software
Ensure that the software on all your devices and servers is up to date. A few days before your assessment is due, take some time to check that all your software has been patched to its latest version and that no unsupported software exists. It’s important to apply high and critical-risk security patches within 14 days of release. This will reduce the risk of unpatched software being detected during the vulnerability scanning.
Check Your Anti-Virus Software Configuration
Make sure your antivirus software on all your devices and servers is up to date and that the signatures are being updated within a 24 hour window. All automatic updates should be turned on where the option is provided. You should also verify that your antivirus software is scanning files on access and also ideally on download.
Check Your Internet-Facing Services
Ensure that any internet-facing services that are no longer required have been disabled. Where any internet-facing services require authentication to access organisation/user data, ensure that the default password has been changed and the service has a form of brute-force attack mitigation in place. This includes an account lockout policy and/or enforcing multi-factor authentication. Where an account lockout mechanism or a form of throttling has been applied, ensure that a user is limited from making more than 10 attempts within a 5-minute period.
Enforce Multi-Factor Authentication for Cloud Service Users
Ensure that multi-factor authentication has been enforced for all users across all cloud services. Where MFA is only available through a premium subscription or has to be applied by using another service to authenticate (such as MS Azure), you will be required to implement this to remain compliant.
Enforce Account Separation for User Accounts
Ensure that any users with access to an administrator account also have a standard user account which is used for day-to-day work. Users must only use the administrator account when conducting necessary tasks such as installing software. Please also ensure that accounts are not shared between multiple users.
How Much Does Cyber Essentials Plus Cost?
The cost of Cyber Essentials Plus can vary a lot across different Certification Bodies.
Predatech offers Cyber Essentials Plus assessment and certification from £1,100+VAT (dependent on organisation size). This includes any support required as well as any re-testing (if applicable).
Please note, Cyber Essentials Plus does require a valid Cyber Essentials certificate (issued in the last three months), and pricing for this can be found here.
Predatech is a CREST-accredited organisation and a Cyber Essentials & Cyber Essentials Plus certification body. If you are interesting in achieving or renewing your Cyber Essentials Plus certification, click here to find out more about our approach or contact us today for a free consultation.




