Wireless access points can provide a gateway into your organisation’s network for unauthorised threat actors.
Understanding the techniques used by threat actors to capture and crack WPA/WPA2 hashes can be also be useful when trying to enhance your network security.
In this blog, we’ll explore how wireless packets can be captured, how WPA/WPA2 pre-shared key hashes can be obtained and how these hashes can be cracked to derive the plaintext password. We’ll then look at what can be done to reduce the risk of wireless exploitation which will ultimately help to better protect your organisation.
Capturing WPA/WPA2 Pre-Shared Key Hashes
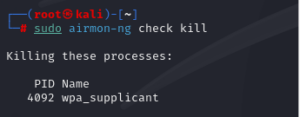
- Kill Running Processes: To begin, you must ensure that any running networking services on your machine are killed. This shuts down any services that may prevent airmon-ng placing the wireless network interface card (NIC) in monitor mode. The following command must be run from the airmon-ng suite.
sudo airmon-ng check kill
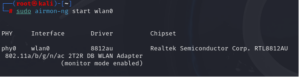
- Monitor Mode Activation: Your wireless NIC must be set to monitor mode. This mode allows the NIC to monitor and capture all wireless traffic within range. We recommend using a wireless adapter that will support packet injection and monitor mode. The wireless adapters will also provide much better signal reception over a built-in wireless NIC.
sudo airmon-ng start wlan0
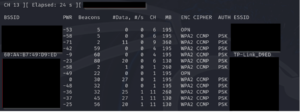
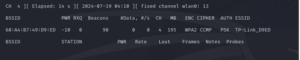
- Packet Sniffing: Once in monitor mode, a tool such as airodump-ng can be employed to capture incoming wireless packets. The tool provides a real-time view of the wireless networks in range (SSIDs) and their access point MAC addresses (BSSIDs). We use the following command, focusing on the wlan0 interface in our case.
sudo airodump-ng ‘wlan0’
- Targeted Capture: To reduce the noise and focus on the target we are interested in, we can set airodump to filter by the relevant BSSID and channel. Where there are multiple BSSIDs, try to focus on one which has a higher amount of data reported.
We now wait until a WPA/WPA2 handshake is captured. Once captured there will be a banner at the top of the panel which reads ‘[ WPA Handshake: <MAC Address>] ’. Once the handshake has been obtained, we can stop the tool and collect the .pcap file that’s been generated (which now holds the captured WPA/WPA2 handshake).
sudo airodump-ng -c 4 –bssid ‘60:A4:B7:49:D9:ED’ -w capture ‘wlan0’
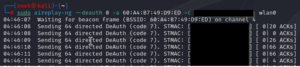
- Deauthentication Attack (Optional): Where you’re having trouble capturing a wireless handshake, you can use a deauthentication attack to expedite the process. By disconnecting a client from the network, you force them to reconnect. This increases your chance of capturing a WPA/WPA2 handshake, particularly where wireless traffic is sparse.
sudo aireplay-ng –deauth 0 -a ‘Access point BSSID’ -c ‘Station BSSID’ ‘wlan0’
Cracking WPA/WPA2 Pre-Shared Key Hashes
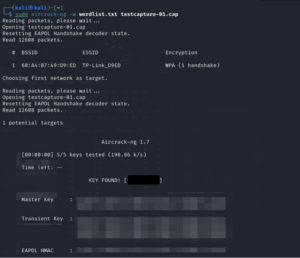
Handshake Cracking: Now that we’ve captured a WPA/WPA2 PSK hash, we can use a tool like aircrack-ng to crack the hash and derive the plaintext password/PSK. This involves running the hash against a common password list.
For this example, I created a .txt file and entered a few lines which included the password for the router. Normally this process would require millions of potential passwords and would take significantly more computing resource and time. The simpler or easier to guess the password is, the higher the likelihood that we’ll get a password match within our list.
sudo aircrack-ng -w ‘wordlist.txt’ ‘capture-01.cap’
How To Reduce The Risk of Wireless Exploitation
Upgrade to WPA3 Where Possible: The WPA3 protocol provides noticeable security benefits over WPA/WPA2, including stronger encryption, forward secrecy and individualised encryption which mitigates the traditional WPA/WPA2 hash capture and cracking techniques. WPA is deprecated and so WPA2 should be used where WPA3 is not an option.
Use Strong & Complex Passwords: Where the WPA2 protocol must be used, ensure that the pre-shared key/WiFi password is strong and not easily guessable. The simpler the password is, the faster it will be cracked if a hash is obtained. Avoid using common words and instead opt for more complex phrases with a mixture of different character types.
Recalibrate Signal Strength: Consider limiting the wireless signal range to only the area practically required. This will make it more difficult for threat actors to pick up a signal from outside the building/premises.
Use a Strong Encryption Algorithm: Where using WPA2, ensure that the settings use the stronger AES encryption rather than TKIP.
Disable SSID Broadcasting: Hide the SSID (wireless network name) by disabling SSID broadcasting. This will make the network less visible to casual threat actors and increase the difficulty for exploitation.
Use MAC Address Filtering: Consider using MAC address filtering to allow only approved devices to be able to connect to the organisation network. Although the MAC address of a device can be spoofed, it makes the process of connecting to the wireless network more difficult for a threat actor.
Predatech is a cyber security consultancy that offers a range of services including CREST accredited penetration testing and Cyber Essentials/Cyber Essentials Plus assessments. What makes us different? We combine expert cyber security with great customer service and value for money. If you’d like to better understand your security posture, and how to strengthen it from attacks including wireless exploitation, please contact us for a free consultation.