In the age of increasingly complex and functionality rich web applications, the tools we use to dynamically test the security of these applications need to be both flexible and intuitive. Sometimes referred to as the ‘Swiss army knife’ of web application security testing, Burp Suite, fits the bill perfectly, and it’s something we use when testing web applications. In this blog we’ll look at what Burp Suite is and some of the key functionality that makes it a must have for anyone dissecting and testing web applications.
What is Burp Suite?
Burp Suite is a Java-based web security testing toolkit developed and maintained by PortSwigger, a global leader in the field of cyber security. Burp Suite has a range of tools that allow you to capture and manipulate web traffic which can help to identify and validate potential attack vectors and vulnerabilities in your web application. Beyond that, Burp Suite also supports a large list of community-built plugins that can be used to extend Burp Suite’s functionality further.
Burp Suite is used heavily during web app penetration testing and provides everything a tester needs to cover the OWASP Top 10 and the techniques in the OWASP WSTG. Burp Suite and its plugins also cater to those looking to automate their testing tasks, offering the ability to create macros and even to write scripts with the help of python.
Burp Suite comes in three editions:
- Burp Suite Community Edition
- Burp Suite Professional Edition
- Burp Suite Enterprise Edition
The Community Edition is free for anyone to download but lacks some features and has some limitations compared to the Professional Edition. However, the Community Edition is more than enough to start learning about how to test and properly secure web applications. Burp Suite has far too much functionality to cover in a brief blog but we’ll focus on some of Burp Suite’s main features and tools that make it such a popular choice for those testing the security of web applications.
Exploring Some of Burp Suite’s Major Functionality and Features
Intercepting Proxy
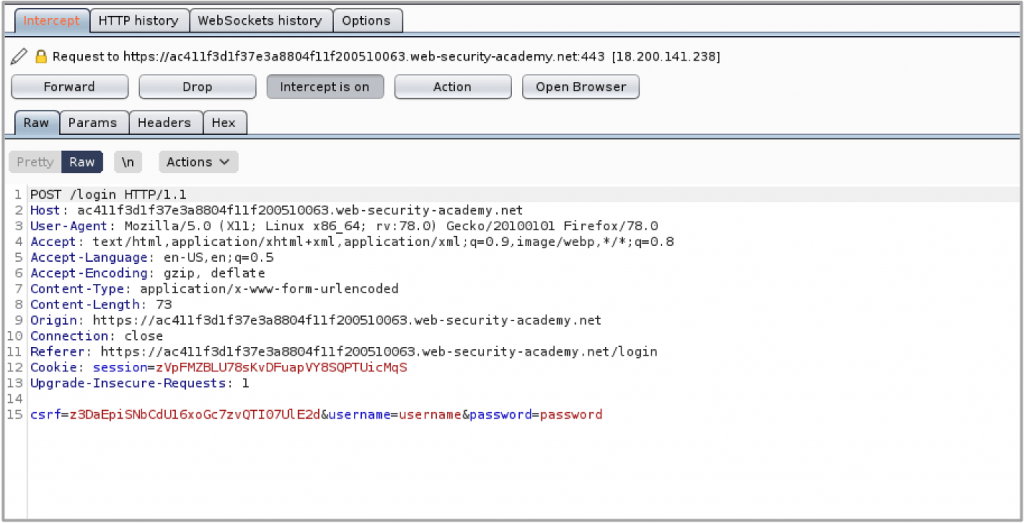
Burp Suite sends receives all the HTTP requests and responses through its web proxy port. This allows the user to capture any HTTP requests being sent to a web application and analyse/manipulate the request before it is sent to the server. All requests and responses received through this proxy are recorded and this makes it simple to understand the workflows of the application at a deeper level.
To get this up and running, you should configure Burp Suite’s certificate on your browser and use a plugin that directs the traffic to Burp Suite’s proxy port and then you’re ready to start capturing traffic.
Target (mapping out the application)
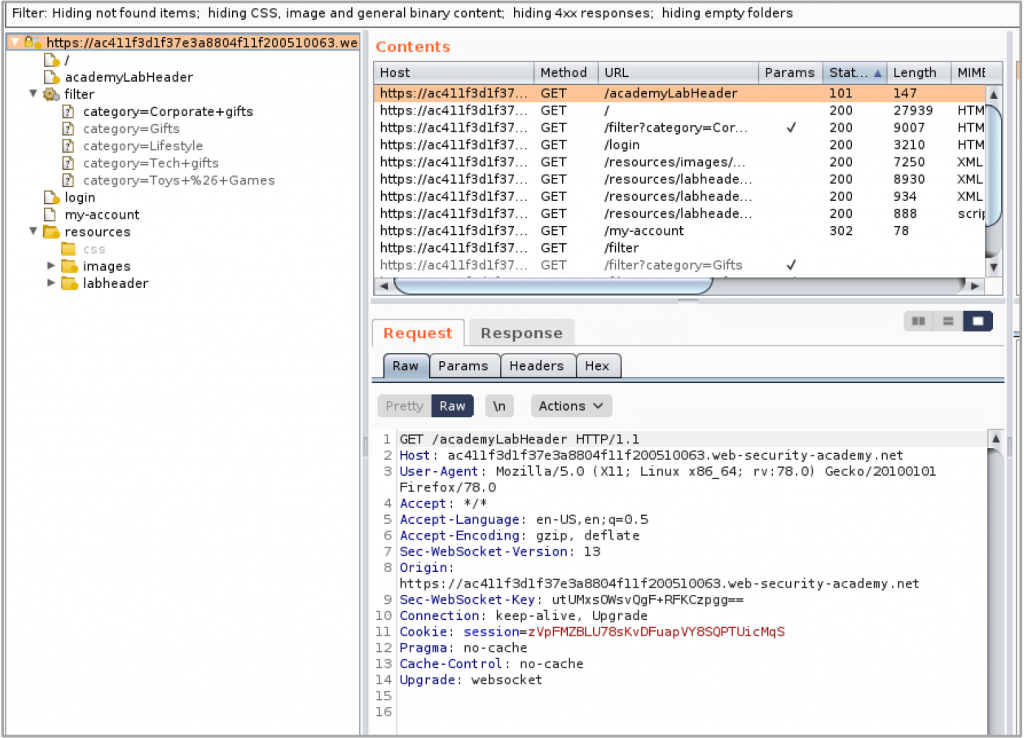
One of the greatest features of Burp Suite is the ability to map out applications. Mapping out an application is typically the first priority when penetration testing an application. As traffic passes through Burp Suite, a site map is formed of all the pages visited. Burp Suite can also passively crawl each page that is visited for references to other pages, allowing you understand all the URLs that each page is linking to. You can also allow Burp Suite to actively crawl any pages it finds as well, giving you the option to crawl manually and/or aided by automatic tools.
When it comes to testing access control and user authorisation, Burp Suite also has you covered as it allows you to compare sitemaps using either two you’ve created yourself, or by requesting all the pages in one sitemap with different cookies and session tokens. This can be helpful in finding what resources are able to be accessed by unauthorised users.
Active and Passive Scanning
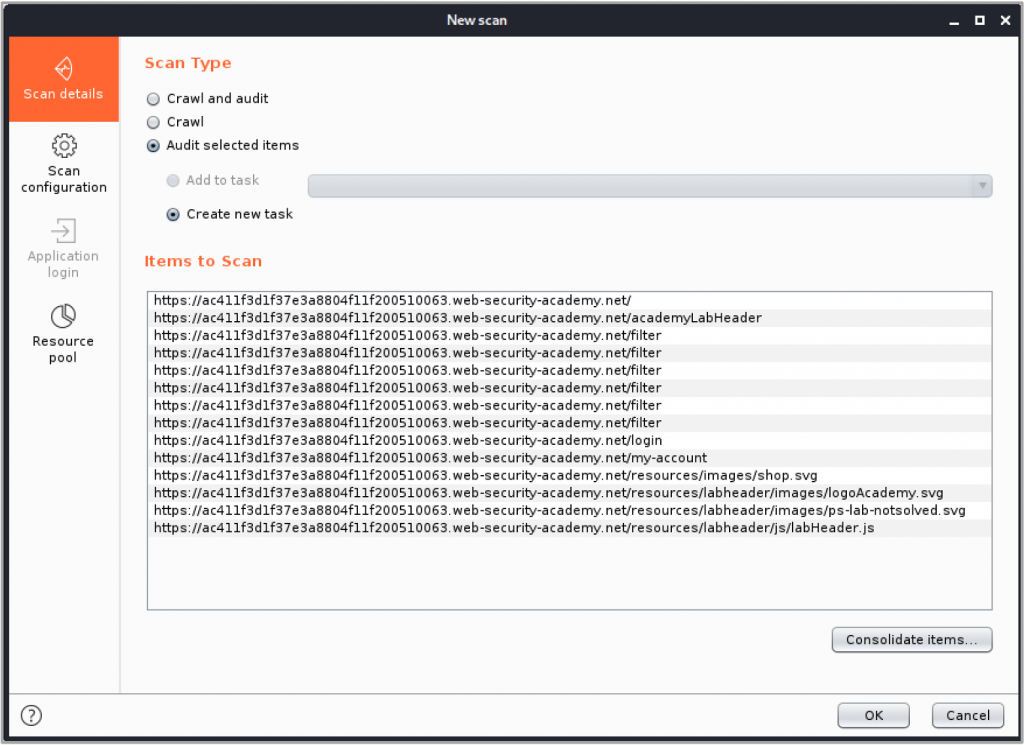
Burp Suite also has built-in scanning capabilities that allows it to dynamically identify potential vulnerabilities and weakness in an application. The passive scan will analyse the data in all the requests and responses it receives to detect vulnerabilities without making any requests itself whereas the active scan will send a number of requests to each resource and analyse the response for a more invasive detection of vulnerabilities.
The scanner allows you to choose what to scan at a resource level, so that you can remove dangerous or disruptive functionality such as a logout request. The scanner can run either with no session token or with a session token specified by the user to ensure that the scan is getting the access it needs to run successfully.
Intruder
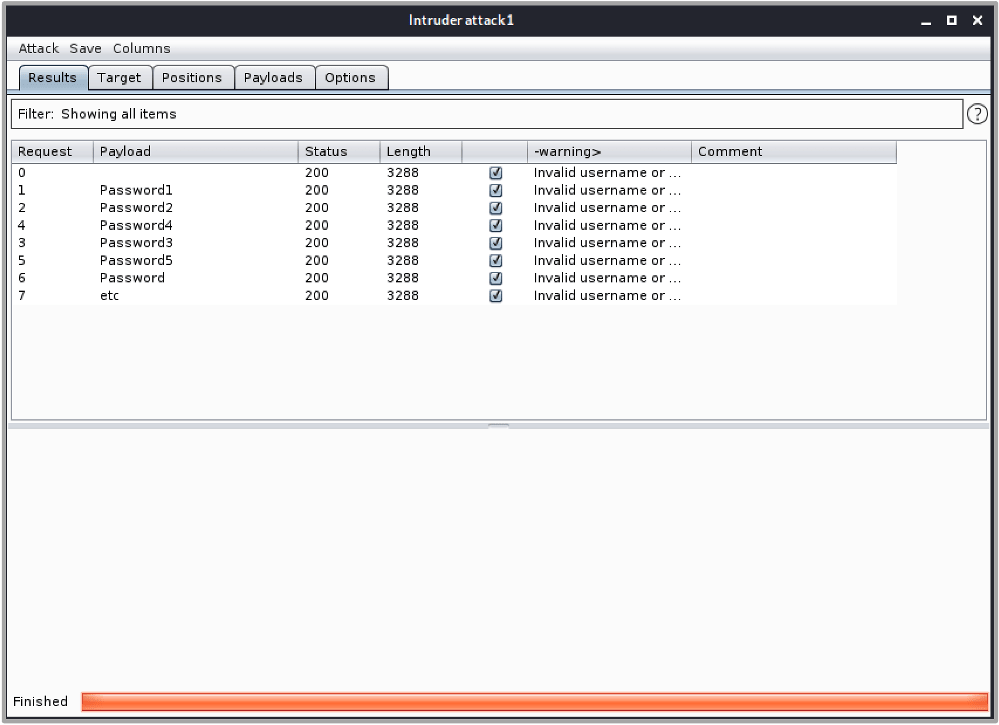
Intruder is one of Burp Suite’s most well-known tools and is used to automate request iterations when given a specific list of payloads. On the surface, Intruder may look like your standard brute-force tool, but it offers so much more.
You can conduct a basic attack with intruder by providing a list of payloads you would like to iterate through and highlighting the areas within the HTTP request where you would like the payloads to be placed. You can then specify how you want Intruder to loop through the payloads in each insertion point and then away it goes. Intruder will then iterate through the payload lists sending a large number of requests.
This can be useful for conducting password spraying attacks against login forms, enumerating users, and looking for valid inputs. And Intruder’s functionality doesn’t stop there; you can use data received from the responses and feed this back into your requests, allowing for more dynamic attacks. There are also plugins such as Turbo Intruder which extend Intruder’s flexibility even further.
Other notable mentions
The features that we’ve mentioned are just a small part of the breadth of functionality and flexibility that Burp Suite offers. Some of the other notable features include:
- Repeater: Allows you to create and modify HTTP requests to send to the server.
- Sequencer: Can help to determine the entropy (randomness) of cookies and session tokens
- CSRF PoC Generator: Burp Suite can generate a proof of concept for a CSRF vulnerability which is code that will exploit that CSRF vulnerability.
- Macros: Allows you to create automated chains of actions including data from the HTTP requests and responses.
Predatech is a cyber security consultancy that offers a range of services including CREST accredited penetration testing and Cyber Essentials/Cyber Essentials Plus assessments. What makes us different? We combine expert cyber security with great customer service and value for money. Please contact us if you’re interested in a free consultation.





